SNMPv3 Explained
SNMPv3 Brief Introduction
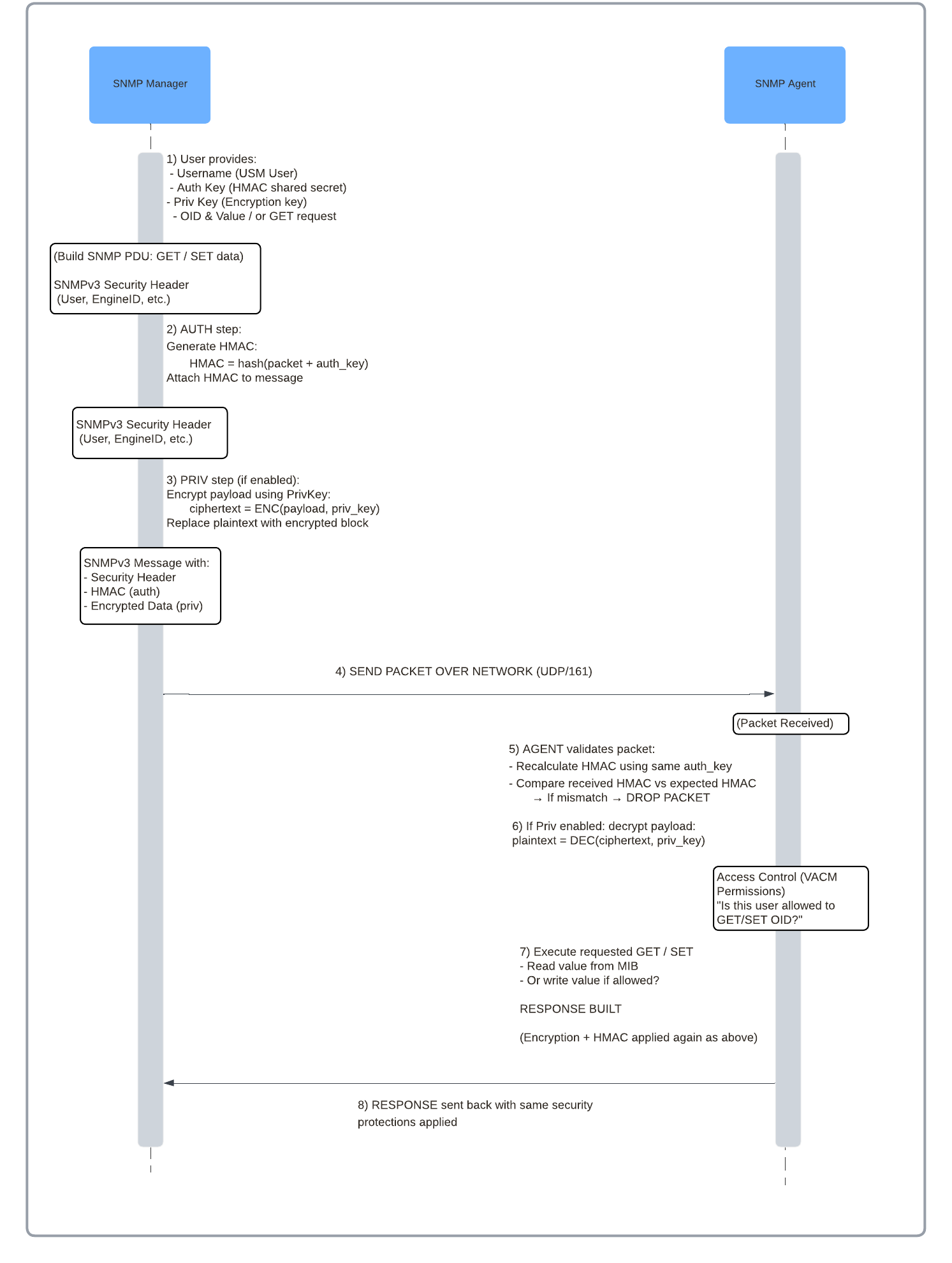
SNMPv3 is the secure version of the Simple Network Management Protocol (SNMP) which allows for communication from a network management system (NMS) or custom SNMP script to a network device or server known as an agent (network devices and servers are the most common use cases).
For many network management systems SNMP is the protocol of choice for monitoring device/agents however are options are available such as RESTCONF and NETCONF however typically found on newer devices and carry a higher network bandwidth load then SNMP. Using SNMP the management system is able to obtain and set data using what is know as Object Identifier (OID) directly to the agent over the network with the management system and agents SNMPv3 credentials needing to match in order for successful communication.
As SNMP uses UDP (User Datagram Protocol) as it’s primary transport protocol it means when SNMP get/set requests are sent they do not require a response from the manager nor agent. With this in mind SNMP does have some measures as network packets can get lost. Some common causes of loss can occur when using microwave radios when the far end link observes some intermittent outages. To counter this with regards to SNMP get and set if the manager does not receive a response in a defined set time it has the ability to retry sending the packet. Common values for timeout are around 30 seconds (though if a response is not received within a second the packet is likely lost) and retry 3 times but these values can be modified if the management system allows.
Some areas to consider when looking at timeout and retries is in bulk network configuration either from the management system or custom SNMP scripts. Depending on the number of devices and network speed high timeout waits can cause the completion of scripts to over run even when using multi threading to distribute the device capture.
What is an OID? (Object Identifier)
An OID (Object Identifier) is a unique numeric address used in SNMP to identify a specific piece of data on a device. Every measurable or configurable value on an SNMP-enabled device—such as hostname, uptime, interface speed, or temperature—is assigned an OID. Vendors of of devices such as network routers need to apply for a unique OID number i.e. 1.3.6.1.4.1.(company number). Once obtained they can start developing unique agent OID's that allow for specific data gathering or setting data.
OIDs are written as dotted numeric paths, for example:
1.3.6.1.2.1.1.5.0
This value points to the device's system name.
OID Structure
OIDs are organized in a hierarchical tree, similar to a directory structure. Each number represents a branch in the tree. For example, the OID above belongs to the system group in the standard SNMP MIB.
Readable Names
Many OIDs also have human-friendly names, such as:
sysDescr.0 → 1.3.6.1.2.1.1.1.0 (Device description)
sysName.0 → 1.3.6.1.2.1.1.5.0 (Device hostname)
SNMP tools can translate between the numeric and named forms automatically.
SNMPv3 Request Types
| Category | Operation | Purpose | Notes |
|---|---|---|---|
| Request | GET | Retrieve the value of one or more OIDs. | Most common monitoring request. |
| Request | GET-NEXT | Retrieve the next OID in the MIB tree. | Used to walk tables sequentially. |
| Request | GET-BULK | Retrieve many OIDs efficiently in a single response. | SNMPv2/v3; reduces multiple GET-NEXTs—great for tables. |
| Request | SET | Modify a value on the agent. | OID must be writable and permitted by VACM/security policy. |
| Response | RESPONSE | Return values or error codes to a request. | Reply to GET / GET-NEXT / GET-BULK / SET. |
| Response (v3) | REPORT | Signal security/engine issues. | SNMPv3 only (e.g., unknown engineID, time sync). |
| Notification | TRAP | Unsolicited event notification. | Agent → Manager, fire-and-forget (no ACK). |
| Notification | INFORM | Reliable notification requiring acknowledgment. | Manager (or agent) expects RESPONSE; SNMPv2/v3. |
SNMPv3 Encryption Options
Authentication (who are you?) via the User-based Security Model (USM)
Privacy/Encryption (keep data confidential) via USM
Authorization (what can you read/write?) via View-based Access Control Model (VACM)
Security levels:
noAuthNoPriv — no auth, no encryption - DO NOT USE THIS METHOD, Essentially it turns a SNMPv3 packet into an unsecured SNMPv2c packet
authNoPriv — authenticated, not encrypted - AGAIN DO NOT USE THIS METHOD, Essentially it allows the agent to accept requests and return data back to the management system however the data is not encrypted and can be read using a packet capture sniffer.
authPriv — authenticated and encrypted (most secure)
SNMPv3 Authentication Protocols
| Protocol | Algorithm | Security Strength | Notes / Usage Guidance |
|---|---|---|---|
| NONE | No authentication | Not secure | Only use on isolated lab setups or testing. Cannot be used with encryption (priv). |
| MD5 | HMAC-MD5 (128-bit digest) | Low | Legacy. Still works widely but considered cryptographically weak. |
| SHA | HMAC-SHA-1 (160-bit digest) | Medium | Common default in many production systems. Better than MD5. |
| SHA224 | HMAC-SHA-224 | Strong | Rarely used but supported in newer SNMP stacks. |
| SHA256 | HMAC-SHA-256 | Strongly Recommended as a minimum | Modern secure choice. Supported in most current SNMPv3 agents. |
| SHA384 | HMAC-SHA-384 | Very strong | High security environments. |
| SHA512 | HMAC-SHA-512 | Very strong | High-security / compliance environments |
SNMPv3 Privacy Protocols
| Protocol | Algorithm | Key Size / Mode | Security Strength | Notes / Usage Guidance |
|---|---|---|---|---|
| NONE | No encryption | N/A | Not secure | Allowed only with noAuthNoPriv or authNoPriv. |
| DES | DES-CBC | 56-bit key | Low | Legacy, weak, but still widely interoperable in older devices. |
| 3DES | Triple-DES EDE | 168-bit key | Medium | More secure than DES, slower than AES. |
| AES / AES128 | AES-CFB-128 | 128-bit key | Strongly recommended as a minimum | Most commonly supported modern choice. |
| AES192 | AES-CFB-192 | 192-bit key | Very strong | Not supported on some older network devices. |
| AES256 | AES-CFB-256 | 256-bit key | Very strong | Highest strength, but support varies depending on vendor/firmware. |
SNMPv3 Authentication and Privacy Workflow